Cryptography and blockchain technology have become increasingly intertwined in recent years, with cryptographic techniques playing a crucial role in the security and functionality of blockchain networks. This blog post will explore the relationship between cryptography and blockchain, the importance of cryptography in securing blockchain, the various cryptographic techniques used in blockchain, and the challenges and future of cryptography in the context of blockchain technology.
Introduction to Cryptography
Cryptography is the practice of securing information and communication through the use of codes and ciphers. It is a fundamental component of modern information security, enabling the protection of sensitive data, ensuring the confidentiality, integrity, and authenticity of information, and enabling secure communication between parties.
The Basics of Cryptography
Cryptography involves the use of various mathematical algorithms and techniques to transform readable information (plaintext) into an unreadable format (ciphertext) that can only be accessed by authorized parties with the correct decryption key. The two main types of cryptographic algorithms are symmetric-key cryptography and asymmetric-key cryptography, also known as public-key cryptography.
Symmetric-Key Cryptography
Symmetric-key cryptography, also known as secret-key cryptography, uses a single shared key for both encryption and decryption. This means that the same key must be known to both the sender and the receiver of the message. Examples of symmetric-key algorithms include AES (Advanced Encryption Standard), DES (Data Encryption Standard), and Blowfish.
Asymmetric-Key Cryptography
Asymmetric-key cryptography, or public-key cryptography, uses a pair of keys: a public key and a private key. The public key is used for encryption, while the private key is used for decryption. This allows for secure communication without the need for a shared secret key. Examples of asymmetric-key algorithms include RSA, Diffie-Hellman, and Elliptic Curve Cryptography (ECC).
Cryptographic Hash Functions
Cryptographic hash functions are another important component of cryptography. These functions take an input message of any length and produce a fixed-length output, called a hash value or message digest. Cryptographic hash functions have several important properties, such as being one-way (it is computationally infeasible to recover the original input from the hash value), collision-resistant (it is computationally infeasible to find two different inputs that produce the same hash value), and deterministic (the same input will always produce the same output). Examples of cryptographic hash functions include SHA-256, MD5, and Blake2.
Introduction to Blockchain Technology
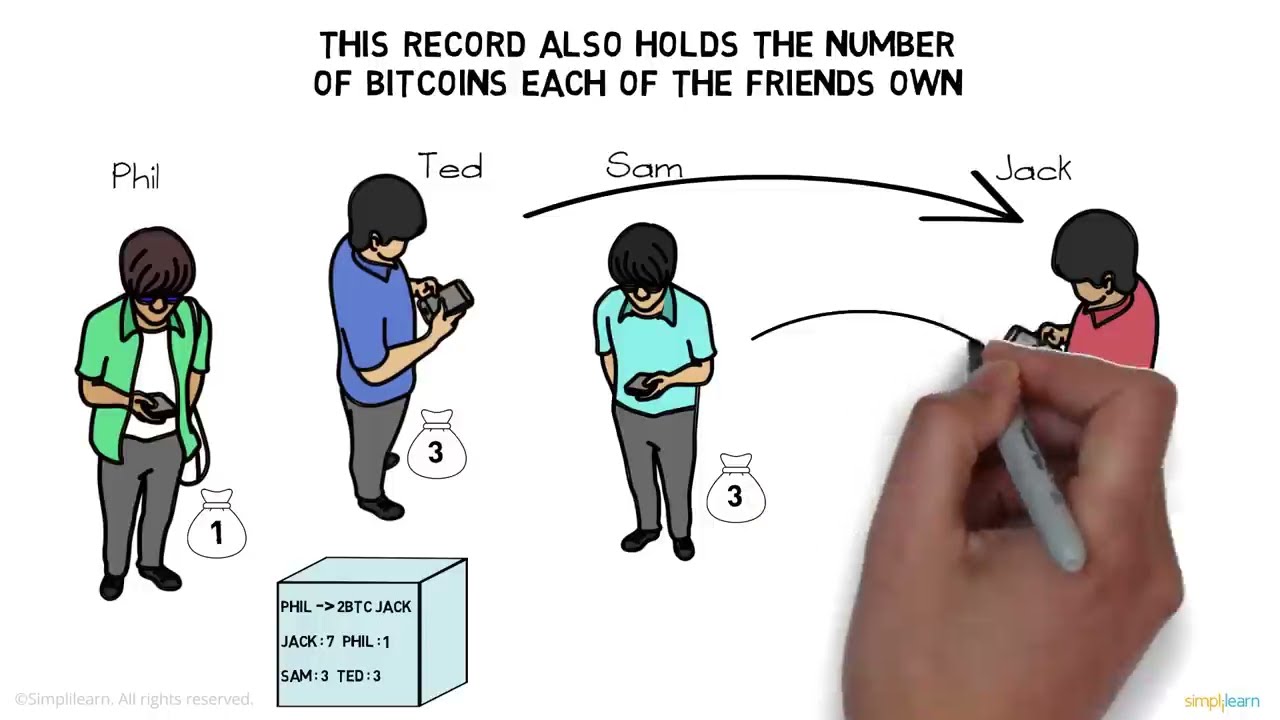
Blockchain technology is a decentralized, distributed digital ledger that records transactions across many computers in a network. Each block in the chain contains a number of transactions, and every time a new transaction occurs, a record of that transaction is added to every participant’s ledger. The decentralized nature of blockchain networks and the use of cryptographic techniques are the key features that make blockchain a secure and transparent technology.
Decentralization and Distributed Ledger
Blockchain is a decentralized system, meaning that there is no central authority or single point of control. Instead, the network is maintained by a distributed network of nodes, each of which maintains a copy of the entire blockchain. This decentralized approach ensures that the network is resilient and resistant to censorship or tampering.
Transactions and Blocks
In a blockchain network, transactions are grouped into blocks, and each block is linked to the previous block through a cryptographic hash. This creates a chain of blocks, hence the name “blockchain”. Each block contains a timestamp, a list of transactions, and a reference to the previous block, which ensures the integrity and chronological order of the ledger.
Consensus Mechanisms
Blockchain networks use consensus mechanisms to ensure that all nodes in the network agree on the state of the ledger. The most common consensus mechanisms are Proof of Work (PoW) and Proof of Stake (PoS). In PoW, nodes compete to solve a complex mathematical problem to add a new block to the chain, while in PoS, nodes with a larger stake in the network have a higher chance of being selected to validate new blocks.
Cryptocurrencies and Smart Contracts
Blockchain technology is often associated with the development of cryptocurrencies, such as Bitcoin and Ethereum. These digital currencies use blockchain to record and verify transactions. Additionally, blockchain can be used to facilitate the execution of smart contracts, which are self-executing contracts with the terms of the agreement between buyer and seller directly written into lines of code.
The Relationship Between Cryptography and Blockchain

Cryptography and blockchain technology are closely intertwined, with cryptographic techniques playing a crucial role in the security and functionality of blockchain networks.
Cryptography in Blockchain
Cryptography is used in blockchain in several ways:
- Public-Key Cryptography: Blockchain networks use public-key cryptography for secure communication, user identification, and transaction signing. Each user has a public key, which is used to identify the user and receive funds, and a private key, which is used to authorize transactions.
- Cryptographic Hash Functions: Blockchain networks use cryptographic hash functions, such as SHA-256 and Keccak-256, to create a secure and tamper-proof record of transactions. The hash values of each block are used to link the blocks together, creating the blockchain.
- Digital Signatures: Blockchain transactions are secured using digital signatures, which are generated using the sender’s private key. This ensures the authenticity and non-repudiation of the transaction.
- Consensus Mechanisms: Cryptographic techniques are also used in the consensus mechanisms that govern the addition of new blocks to the blockchain. In Proof of Work, nodes compete to solve a complex cryptographic puzzle to add a new block, while in Proof of Stake, the validation of new blocks is based on the stake (i.e., the amount of cryptocurrency) held by the node.
The Importance of Cryptography in Blockchain
Cryptography is essential to the security and integrity of blockchain networks. The use of cryptographic techniques ensures the following:
- Data Integrity: Cryptographic hash functions ensure that the blockchain data cannot be tampered with, as any modification to the data would result in a different hash value, which would be immediately detected by the network.
- Confidentiality: Public-key cryptography enables secure communication and the protection of sensitive data, such as transaction details, within the blockchain network.
- Authentication and Non-Repudiation: Digital signatures provide a way to authenticate the origin of transactions and ensure that the sender cannot deny their involvement.
- Consensus and Integrity: Cryptographic techniques, such as those used in Proof of Work and Proof of Stake, ensure the integrity of the consensus process and prevent network attacks, such as double-spending.
Importance of Cryptography in Securing Blockchain
Cryptography is the foundation of blockchain security, and its role in securing blockchain networks cannot be overstated. Here are the key ways in which cryptography helps secure blockchain technology:
Ensuring Data Integrity
Cryptographic hash functions are used to create a secure, tamper-evident record of transactions in the blockchain. Each block in the chain contains a cryptographic hash of the previous block, which links the blocks together and ensures that the data cannot be altered without detection. If an attacker tries to modify a transaction in the blockchain, the hash value of the affected block will change, and the network will reject the modified block.
Providing Confidentiality
Blockchain networks use public-key cryptography to protect the confidentiality of transaction data. Sensitive information, such as the details of a transaction or the identities of the parties involved, can be encrypted using the recipient’s public key. Only the intended recipient, who holds the corresponding private key, can decrypt the information.
Enabling Authentication and Non-Repudiation
Digital signatures, which are based on public-key cryptography, play a crucial role in blockchain security. When a user initiates a transaction, they sign the transaction data with their private key. This digital signature serves as proof of the user’s identity and ensures that the transaction cannot be repudiated, as only the user with the correct private key could have generated the signature.
Securing Consensus Mechanisms
Cryptographic techniques are integral to the consensus mechanisms used in blockchain networks. In Proof of Work, the mining process involves solving complex cryptographic puzzles, which ensures that the creation of new blocks is computationally expensive and prevents Sybil attacks, where an attacker tries to take control of the network by creating multiple identities. In Proof of Stake, the validation of new blocks is based on the stake (i.e., the amount of cryptocurrency) held by the node, which is secured using cryptographic techniques.
Defending Against Attacks
Cryptography helps defend blockchain networks against various types of attacks, such as:
- Double-Spending Attacks: Cryptographic hash functions and digital signatures prevent double-spending, where an attacker tries to spend the same cryptocurrency twice.
- 51% Attacks: The computational complexity required to solve the cryptographic puzzles in Proof of Work makes it extremely difficult for an attacker to control more than 50% of the network’s computational power, which is necessary to execute a 51% attack.
- Sybil Attacks: The use of public-key cryptography and digital signatures makes it difficult for an attacker to create multiple identities and take control of the network.
Cryptographic Techniques Used in Blockchain
Blockchain technology utilizes a variety of cryptographic techniques to ensure the security and integrity of the network. Here are some of the key cryptographic techniques used in blockchain:
Public-Key Cryptography
Public-key cryptography, also known as asymmetric-key cryptography, is the foundation of many blockchain security features. In blockchain, public-key cryptography is used for the following purposes:
- User Identification: Each blockchain user has a public key, which serves as their unique identifier on the network. The public key is used to receive transactions and is publicly visible, while the private key is used to authorize and sign transactions.
- Transaction Signing: When a user wants to initiate a transaction, they use their private key to digitally sign the transaction data. This signature is then included in the transaction, and other nodes can verify the authenticity of the transaction using the signer’s public key.
- Secure Communication: Public-key cryptography can also be used to encrypt communication between nodes in the blockchain network, ensuring the confidentiality of sensitive information, such as transaction details.
Cryptographic Hash Functions
Cryptographic hash functions play a crucial role in the integrity and security of blockchain networks. The most commonly used hash functions in blockchain are SHA-256 and Keccak-256 (also known as SHA-3). These hash functions are used in the following ways:
- Block Hashing: Each block in the blockchain contains a cryptographic hash of the previous block, creating a secure, tamper-evident chain of blocks.
- Proof of Work: In the Proof of Work consensus mechanism, miners compete to solve a complex cryptographic puzzle, which involves finding a hash value that meets a certain difficulty target.
- Digital Signatures: Cryptographic hash functions are used in the process of creating and verifying digital signatures, which are used to authenticate transactions.
Digital Signatures
Digital signatures, which are based on public-key cryptography, are a crucial component of blockchain security. They are used to:
- Authenticate Transactions: When a user initiates a transaction, they sign the transaction data with their private key. Other nodes can then verify the authenticity of the transaction by checking the digital signature using the signer’s public key.
- Ensure Non-Repudiation: The use of digital signatures ensures that the sender of a transaction cannot later deny their involvement, as the signature is cryptographically linked to the sender’s private key.
- Maintain Integrity: If an attacker tries to modify a transaction, the digital signature will no longer match the transaction data, and the network will reject the modified transaction.
Consensus Mechanisms
Cryptographic techniques are also used in the consensus mechanisms that govern the addition of new blocks to the blockchain. The two most common consensus mechanisms are:
- Proof of Work (PoW): In PoW, miners compete to solve a complex cryptographic puzzle, known as the “hash puzzle”. The first miner to solve the puzzle is rewarded with the right to add a new block to the blockchain.
- Proof of Stake (PoS): In PoS, the validation of new blocks is based on the stake (i.e., the amount of cryptocurrency) held by the node. Nodes with a larger stake have a higher chance of being selected to validate new blocks, and their selection is secured using cryptographic techniques.
Challenges and Future of Cryptography in Blockchain Technology
While cryptography is the foundation of blockchain security, there are still some challenges and areas for improvement in the use of cryptographic techniques in blockchain technology.
Scalability Challenges
One of the key challenges in blockchain is scalability, and cryptographic techniques can play a role in both the problem and the solution. The computational complexity of the cryptographic puzzles used in Proof of Work consensus mechanisms can limit the throughput and transaction processing speed of blockchain networks. This has led to the development of alternative consensus mechanisms, such as Proof of Stake, which aim to reduce the computational requirements while still maintaining the security of the network.
Quantum Computing Threats
The advent of quantum computing poses a potential threat to the security of many cryptographic algorithms used in blockchain. Quantum computers have the potential to break the mathematical problems that underpin public-key cryptography, such as the integer factorization problem used in RSA. This could allow attackers to forge digital signatures, impersonate users, and potentially even rewrite the blockchain history. Blockchain networks are working to develop quantum-resistant cryptographic algorithms to mitigate this threat.
Privacy Concerns
While blockchain provides a high degree of transparency, there are also concerns about the privacy of transactions and user identities. Although blockchain addresses do not directly reveal the real-world identities of users, there are still ways to potentially link addresses to individuals. Researchers are exploring the use of advanced cryptographic techniques, such as zero-knowledge proofs and ring signatures, to enhance the privacy of blockchain transactions without compromising the integrity of the network.
Regulatory Compliance
As blockchain technology matures and is adopted by more industries, there will be an increasing need for blockchain systems to comply with various regulatory requirements, such as data protection laws and financial regulations. Cryptographic techniques will play a crucial role in ensuring that blockchain networks can meet these compliance requirements, particularly in areas such as data encryption, access control, and auditing.
Ongoing Cryptographic Research and Innovation
The field of cryptography is constantly evolving, with researchers and developers continuously working to create new, more secure algorithms and techniques. As blockchain technology continues to grow and evolve, it will be important for the blockchain community to stay informed about the latest advancements in cryptography and to incorporate them into the design and implementation of blockchain networks. This could include the adoption of post-quantum cryptography, the development of new consensus mechanisms, and the integration of advanced privacy-preserving techniques.
Conclusion
In conclusion, cryptography is the foundation of blockchain technology, playing a crucial role in ensuring the security, integrity, and functionality of blockchain networks. The use of cryptographic techniques, such as public-key cryptography, cryptographic hash functions, and digital signatures, enables the secure recording of transactions, the authentication of users, and the protection of sensitive information.
As blockchain technology continues to evolve and be adopted in a wide range of applications, the importance of cryptography in this field will only continue to grow. Addressing the challenges and embracing the ongoing advancements in cryptography will be essential for the future development and widespread adoption of blockchain technology.

